References to cybersecurity conjure IT concerns of ransomware or theft of proprietary data from company servers. Instead, imagine a factory floor full of networked machines. In an Industry 4.0 world, protecting OT assets is just as important as protecting IT assets.
This April, the United States government issued a Cybersecurity Advisory (CSA) about threats of bad actors accessing and/or taking control of industrial control systems (ICS) supervisory control and data acquisition (SCADA) devices and programmable logic controllers (PLCs.) Criminals could exploit systems to upload malicious code, modify device parameters and break network connections among other nuisances that may or may not cost companies a lot of money to address.
Unfortunately, just as cybersecurity experts lament companies not acknowledging the risks of and taking protection against IT cyberthreats, Fortinet’s 2022 State of Operational Technology and Cybersecurity Report, based on a worldwide survey of over 500 OT security professionals, shows that companies lag in their strategies to protect OT. Only 13% of respondents have centralized visibility of all OT activities and only 52% track all OT activities from a security operations center (SOC).
In other words, 87% of respondents can’t easily see their OT network activities from devices, users and applications generally and 48% do not leverage the insights from security experts in their SOC to quickly detect and respond to cyberattacks. And all of this when 93% of respondents experienced an OT intrusion in the last 12 months and 78% experienced more than three intrusions.
“Traditionally, security wasn’t a concern for operational technology networks since they were air-gapped from IT networks and relied on components and control languages that few other than engineers or OT programmers used. In other words, they relied on security through inaccessibility and obscurity,” says Jim Richberg, field CISO for public sector at Fortinet.
“However, OT networks have increasingly been connected to IT networks by the enterprises that own them for reasons of cost, efficiency, productivity, and profitability,” Richberg continues. “While this interconnectedness has brought benefits, it has made OT networks potentially accessible from anywhere via the Internet. In addition, malicious software designed to exploit OT components and control languages has become increasingly available for purchase or even rental by malicious cyber actors. As a result, OT networks are increasingly accessible and exploitable targets.”
Recognizing and Preparing Against OT Cyberthreats
Fortinet found that investment in OT-specific cybersecurity increased faster than spending on IT-only cybersecurity, with projected compound annual growth rates of 21% for OT security and 16% for OT/IT security between now and 2027.
Ransomware, the largest cybersecurity concern cited by two-thirds of respondents globally, was also cited by 75% of North American respondents specifically. Compliance management and monitoring solutions were cited most commonly as the most important cybersecurity solution respondents deployed, with OT-specific protocol protection features ranking second.
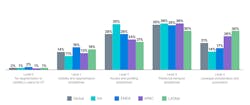
Fortinet says that on a five-level scale of OT security posture readiness, 70% of organizations in North America operate at the middle level. Unfortunately, the number of North American organizations that have 100% visibility of their OT operations has decreased from 23% in 2020 to 13% in 2022.
Frequency and Severity of OT Cyberattacks
Looking specifically at North American results, 48% of respondents reported having three or more cybersecurity intrusions per year. The number of respondents experiencing 10 or more intrusions declined from 12% to 5% year over year, however. Malware and phishing attacks were most commonly reported, hitting 40% of organizations. Less than a third were hit with ransomware attacks.
Demonstrating the point about the need to pay attention to OT security needs specifically, 61% of intrusions impacted OT while 60% impacted IT. Almost half the respondents had operational outages that affected productivity and 90% of respondents stated it took hours or longer to return to service. Unsurprisingly, the report also indicates that the more mature a company’s cybersecurity policies, the more likely they return to service only in minutes.
Best OT Cybersecurity Practices
By analyzing the data from organizations that had zero cybersecurity intrusions over the past 12 months and comparing them to data from organizations that had more than 10 intrusions, Fortinet researchers drew some conclusions about best practices for OT cybersecurity.
· Make OT activities centrally visible to cybersecurity operations
· Hold security vulnerability response time as a top three metric for success
· Use role-based network access control technology
· Report security compromises to executive leadership
· Allow the SOC to monitor and track OT cybersecurity
· Track and report intrusions detected and remediated
· Use a single vendor for IP-related OT devices
You may view and download the full report on the Fortinet website.
About the Author
Dennis Scimeca
Dennis Scimeca is a veteran technology journalist with particular experience in vision system technology, machine learning/artificial intelligence, and augmented/mixed/virtual reality (XR), with bylines in consumer, developer, and B2B outlets.
At IndustryWeek, he covers the competitive advantages gained by manufacturers that deploy proven technologies. If you would like to share your story with IndustryWeek, please contact Dennis at [email protected].