What do Molson Coors, Bombardier, Kia Motors, Palfinger, Foxconn, Steelcase, Nissan, Solarwinds, KYB Corp., CMA CGM, Tesla and Honda all have in common? Each has made news in recent months for allegedly falling victim to a cyber security incident. And, unfortunately, the list keeps growing.
Simply put, cyber security is a growing issue within an increasingly digital world. And as this recent flurry of events has shown, manufacturers are right in the center of the crosshairs for many of today’s highly sophisticated hackers.
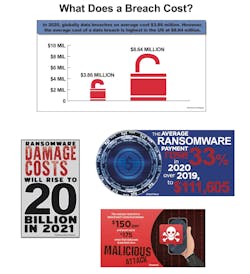
The scary part? There is a big difference between recognizing when an attack occurs and containing it. According to the Ponemon Institute’s latest Cost of a Data Breach, it took companies on average 207 days to identify and 73 days to contain a breach - a total of 280 days last year. This is up from 279 days to identify and contain a breach the previous year. Unfortunately, remediation and rebuilding trust is often the most costly aspect of a comprehensive attack.
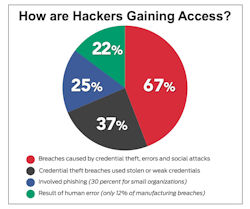
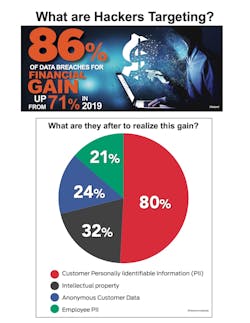
As hackers become increasingly sophisticated, access to new tools and attack methods have enabled them to gain access to more records and in the case of manufacturers avenues to potentially controlling connected equipment. However, the technique most commonly leveraged was stolen credentials, accounting for over 79 percent of hacking breaches; 33 percent of breaches were associated with either phishing or pretexting.
About the Author
Peter Fretty
Technology Editor
As a highly experienced journalist, Peter Fretty regularly covers advances in manufacturing, information technology, and software. He has written thousands of feature articles, cover stories, and white papers for an assortment of trade journals, business publications, and consumer magazines.